Overview
What is Carbon Black Endpoint?
The VMware Carbon Black Endpoint solution (formerly Cb Defense) is an endpoint security and "next-gen antivirus (NGAV)" that uses machine learning and behavioral models to analyze endpoint data and uncover malicious activity to stop all types of attacks before they…
Your best offense against malicious endpoint activity is to be found with CB Defense
Best "Bang for the Buck" in the NGAV field
Cb Defense Provides Next Gen Security with great visiblity into what is occuring on your EndPoints
CB Defense with Live Response ....What a wonder
Cb Defense: Grab your threat hunting gear!
Cb Defense NGAV
Cb Defense Stops Bad Guys Cold
Pricing
What is Carbon Black Endpoint?
The VMware Carbon Black Endpoint solution (formerly Cb Defense) is an endpoint security and "next-gen antivirus (NGAV)" that uses machine learning and behavioral models to analyze endpoint data and uncover malicious activity to stop all types of attacks before they reach critical systems. Endpoint…
Entry-level set up fee?
- No setup fee
Offerings
- Free Trial
- Free/Freemium Version
- Premium Consulting/Integration Services
Would you like us to let the vendor know that you want pricing?
57 people also want pricing
Alternatives Pricing
What is Kaspersky EDR Optimum?
Kaspersky Endpoint Detection and Response (EDR) Optimum helps identify, analyze and neutralize evasive threats by providing easy-to-use advanced detection, simplified investigation and automated response. It is a basic EDR tool for mid-market organizations who are just starting to build their…
What is Kaspersky EDR Expert?
Kaspersky Endpoint Detection and Response (EDR) Expert provides endpoint protection, advanced detection, threat hunting and investigation capabilities and multiple response options in a single package. It is an EDR solution for IT security teams with more mature incident response processes,…
Product Details
- About
- Competitors
- Tech Details
- Downloadables
- FAQs
What is Carbon Black Endpoint?
Carbon Black Endpoint Screenshots
Carbon Black Endpoint Video
Carbon Black Endpoint Competitors
- Symantec Endpoint Security
- Sophos Intercept X
- Trend Micro Apex One
- McAfee Antivirus
Carbon Black Endpoint Technical Details
| Deployment Types | On-premise, Software as a Service (SaaS), Cloud, or Web-Based |
|---|---|
| Operating Systems | Windows, Linux, Mac |
| Mobile Application | No |
| Supported Languages | English |
Carbon Black Endpoint Downloadables
Frequently Asked Questions
Comparisons
Compare with
Reviews and Ratings
(29)Community Insights
- Business Problems Solved
- Pros
- Cons
Cb Defense by VMware Carbon Black Endpoint is used by organizations across various industries to address their endpoint security needs. With its advanced threat protection and management capabilities, the product serves as the primary antivirus agent, monitoring and protecting all endpoints from both known and unknown malware threats. Customers have reported that Cb Defense effectively stops 0-day threats and provides better protection compared to previous solutions against antivirus, malware, spyware, and potentially unwanted programs.
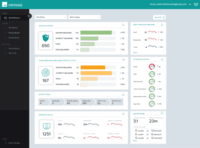
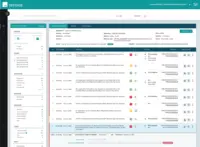
One key use case of Cb Defense is its ability to enable threat hunting and investigations through its advanced forensics capabilities. Users have found that the product goes beyond traditional threat prevention by offering tools to contain and track active threats. The Dashboard provides visibility into process executions and system history, allowing users to identify anomalies and take appropriate actions. This has been particularly useful in addressing potential endpoint infections and compromises in security.
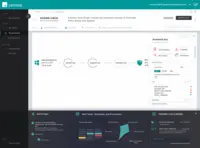
Organizations have also found value in Cb Defense for its easy deployment and management, providing a seamless experience for users. It has replaced insufficient endpoint protection products across multiple lines of business within organizations. Users appreciate the next-gen AI capabilities and non-pattern-based approach to threat detection and prevention offered by Cb Defense.
Moreover, the introduction of version 3.2.2 has enhanced the deployment strategy by offering features such as the ability to quarantine endpoints and perform live analysis on systems. This has provided users with greater control and flexibility in managing potential threats. Additionally, Cb Defense plays a critical role in supporting PCI compliance initiatives, ensuring that organizations meet regulatory requirements.
Overall, customers have found Cb Defense to be an effective solution for their endpoint security needs. Its advanced threat protection, threat hunting capabilities, ease of use, and compliance support make it a valuable addition to any organization's security portfolio.
Dashboard's Helpful Monitoring: Users have found the Carbon Black Endpoint's Dashboard to be extremely helpful in monitoring process execution history and identifying malicious activities. Several reviewers have mentioned that it allows for easy detection of malware, backdoor, rootkit, or Trojan infections.
Quarantine Capability: The ability to quarantine a system directly from the Dashboard has been highly appreciated by users. This feature eliminates the need for manual intervention and allows for immediate analysis and response. Multiple reviewers have praised this functionality.
Seamless Live Response Integration: Reviewers have praised Carbon Black Endpoint's seamless integration of Live Response with the quarantine capability. This feature enables efficient analysis and troubleshooting directly from the user's workstation, eliminating additional steps such as pulling drives or creating hard drive images. Many users have spoken positively about this integrated functionality.
Integration with SIEM products needs improvement: Several users have expressed frustration with the integration capabilities of VMware Carbon Black Endpoint, particularly when it comes to Alien Vault and other SIEM products like Splunk. They have mentioned that detailed setup instructions are lacking, making it difficult to integrate effectively. This is especially problematic for organizations with multiple USM appliances.
Concerns about data leakage and third-party access: Some reviewers have raised concerns about the security of their data collected by the software. They have mentioned that the system uploads data to the cloud on port 443, which raises questions about potential visibility to third parties. These concerns highlight a need for clearer communication and reassurance regarding data privacy.
False positive alerts: A number of users have reported experiencing false positive alerts generated by VMware Carbon Black Endpoint. Examples include Outlook scraping memory being flagged as ransomware activity or triggers from Word, Excel, and Chrome resulting in unnecessary alerts. While some reviewers suggest whitelisting within the alert itself, they express a lack of time for manual actions required to address these false positives efficiently.
Attribute Ratings
Reviews
(1-4 of 4)Your best offense against malicious endpoint activity is to be found with CB Defense
- It uses a thin, low-performance consuming, client.
- It constantly monitors endpoint activity and processes, efficiently, and effectively blocking harmful apps.
- It not only identifies and blocks apps known to be harmful, but prevents unknown, suspicious processes/apps from executing unless allowed in a defined policy.
- It does not offer a way to scan individual files on your endpoint. Some users like to be able to do this. Personally, given the effectiveness of the agent, I don't see a need for this, but it would appease some users.
- Anti-Exploit Technology
- 100%10.0
- Endpoint Detection and Response (EDR)
- 100%10.0
- Centralized Management
- 100%10.0
- Hybrid Deployment Support
- N/AN/A
- Infection Remediation
- 100%10.0
- Vulnerability Management
- 100%10.0
- Malware Detection
- 100%10.0
- By reducing the instances of infections, and so the cost of remediation, we have already realized a better ROI than with prior solutions of this kind.
- In providing a cloud-based management portal, we are better able to manage the protection of our endpoints regardless of their connectivity to our LANs.
- We are also able to prevent unauthorized apps from launching, giving us another way to conform endpoint use to company policies.
Cb Defense Provides Next Gen Security with great visiblity into what is occuring on your EndPoints
- Cb Defense does a great job of monitoring the endpoint activities in great detail.
- Defense is a cloud-based offering and has an easy to use centralized interface.
- The alerts are very definable, and as such are easily refined to avoid getting too many extraneous alerts.
- The Cb salespeople have been very accommodating to get to price points that we as an SMB (with tight budgets) could afford.
- We have only needed support on a couple occasions (which is a positive), but they weren't able to really resolve either issue.
- This brings me to my second con, which is that we have only used three sensor packages (the installed client) and have had issues crop up with two out of three.
- Anti-Exploit Technology
- 90%9.0
- Endpoint Detection and Response (EDR)
- 90%9.0
- Centralized Management
- 90%9.0
- Infection Remediation
- 90%9.0
- Vulnerability Management
- 90%9.0
- Malware Detection
- 90%9.0
- Like most security products, we keep layering on there isn't an ROI. We simply spend more and more.
- The positive cost aspect of Cb Defense is that, compared to other endpoint protection we have paid for, you seem to get a lot of value for the money at only slightly higher costs.
CB Defense with Live Response ....What a wonder
With the introduction of 3.2.2, The live response has given new meaning to our deployment strategy. We now have the ability to quarantine the endpoint and perform live analysis on the system. To give you an idea, if a system has triggered an alarm, we can login to the Dashboard, and see all the process executions, and a history of the system. If we see something "out of the norm" we can quarantine the system, access it remotely, and dump the memory, and transfer tools such as sys internals, and volatility to perform deeper analysis.
- History of Process Execution, really anything that happens in the system is easily seen within the Dashboard. I can determine if a bad actor has infected the system, be it malware, backdoor, rootkit, Trojan, then from that point, I can put the system into Quarantine.
- Being able to quarantine the system from the Dashboard. With these type of tools, pulling the power and running a hard drive image is not needed. Put the system in quarantine, start the analysis. A year ago, the network engineer might move the system into a VLAN that has no access to anything, except the system performing the remote analysis... Now I do not have to rely on anyone to move a system, power it down, pull the drive, or image the drive. I can just start the analysis right from my workstation.
- The Live Response, again goes hand in hand with the quarantine feature.
- By now, I am sure you see a process. Its simple, and easy and all done from a cloud-based console, called the dashboard. .. deploy the agent, create the policy, and active live response, set up email alerts, and monitor your endpoints... you are now ready to perform a triage in the event of an infection. We have step 1, step 2, step 3... but, just remember, things do happen, nothing is perfect, but this product has its advantages.
- I would like to see better integration with Alien Vault, other SIEM products such as Splunk has detailed instruction on the setup, but since we have 3 USM appliances within our organization, the integration would be key for us.
- Some say that data leakage occurs from collecting information being sent to the cloud. The way the system works is it basically looks at a system and decide after time what is normal process execution, then uploads this data on port 443 to the cloud. I have read that this data can be seen by 3rd parties, but I haven't seen it myself.
- ref: https://www.directdefense.com/harvesting-cb-response-data-leaks-fun-profit/
- Sometimes I get some crazy alerts like Outlook has scraped memory due to Ransomware. Other times it's Word or Excel, even Chrome. I could go into the policy and start whitelisting, which by the way, whitelisting can be done within the alert, but who has time.
Well suited for process and memory monitoring.
Less appropriate for smaller organizations.
- It actually stooped a memory scraper from stealing credit card data from our POS system. The casino was bought from awhile back, so coming into this place 4 years ago, we had a flat network. Not good with POS System. Well, a memory scraper was released (employee downloaded a game) and Cb Defense just killed it... This was before a live response, so we pulled the system from the network.
- I can't really say anything negative, at least from an ROI point of view.
Cb Defense: Grab your threat hunting gear!
- It's Cloud based. Has reduced our on premise server footprint. Has also reduced all the management overhead. Specifically, frequent updates/upgrades. Mobile devices don't need to be connected to our network.
- Threat hunting and analysis. We are able to see a ton of forensic information.
- Management interface is intuitive and easy to use.
- Tighter integration with its other products like Cb Protect.
- More specific controls for FIM.
- A definite positive impact. It has decreased the amount of resources needed to manage an on-prem solution.
- It has increased our ability to defend against and react to advanced threats.